Configure HULFT Square to log in with SSO
HULFT Square supports single sign-on (SSO) that uses Microsoft ADFS (Active Directory Federation Service) and Microsoft Entra ID (formerly Azure Active Directory).
In order to be able to log in with SSO, first configure ADFS or Microsoft Entra ID, and then configure SSO in HULFT Square.
For details about how to configure ADFS, refer to Set up ADFS to log in with SSO in the tutorials.
For details about how to configure Microsoft Entra ID, refer to Set up Microsoft Entra ID (formerly Azure Active Directory) to log in with SSO in the tutorials.
This scenario describes the settings that HULFT Square administrators need to configure to enable SSO in HULFT Square.
Description
Points for using SSO
Because HULFT Square manages users by groups, all users must belong to a group. If a user who doesn't have a HULFT Square account logs in to HULFT Square for the first time with SSO, a user account is created when that user logs in. That user must be assigned to a group.
In this tutorial, you will create a security group on the Active Directory side or the Microsoft Entra ID side to which SSO users belong and map them to the group on the HULFT Square side so the users are mapped to the specified group.
-
In order to configure SSO, the SSOFullAccess policy, which contains the ViewSSO and EditSSO permissions, needs to be assigned.
-
Users with SSO enabled can't log in by password or multifactor authentication (MFA).
When users with SSO enabled log in to HULFT Square using SSO, the following functions are disabled:
-
Multifactor authentication
-
Invitation of users
-
Password change
-
Password policy
-
-
As a precaution in case the SSO function becomes unusable, SSO isn't enabled for users who have the EditSSO permission. They must always log in with a password.
It's strongly recommended that they ensure security by taking measures such as also using multifactor authentication.
-
The username is case sensitive.
Steps and what to do
If this is your first time using SSO, it's recommended to apply SSO to a specific group of users first to confirm the usability before applying it to all users. This tutorial is described as a scenario in which you enable SSO for a specific group and then enable SSO for all groups.
Perform the work in the following procedures:
Procedures
Enable SSO for a specific group
To check the usability when SSO is enabled, enable SSO for a specific group.
(1) Set up ADFS or Microsoft Entra ID (formerly Azure AD) to log in with SSO
For the ADFS setup procedure to log in with SSO, refer to Set up ADFS to log in with SSO in the tutorials.
For the Microsoft Entra ID setup procedure to log in with SSO, refer to Set up Microsoft Entra ID (formerly Azure Active Directory) to log in with SSO in the tutorials.
(2) For users who configure SSO, set the EditSSO permission
For details about how to set policies to users and groups, refer to Set up users and groups.
(3) Enable SSO for a specific group
-
Select
 > USER MANAGEMENT > Single Sign-On.
> USER MANAGEMENT > Single Sign-On. -
On the Single Sign-On page, select Edit.
-
On the edit page of Single Sign-On, specify the SSO information.
Set the following values here and select Apply.
Field name
Setting (example)
Status
On - Specific Group
Group
HULFT_Square_Users
IdP
ADFS or Microsoft Entra ID
Email domain
Set the email domain of the organization which you belong to.
Federation metadata URL
-
For ADFS
https://<adfs-server-url>/FederationMetadata/2007-06/FederationMetadata.xml
-
For Microsoft Entra ID
Enter the value for App Federation Metadata Url under SAML Certificates.
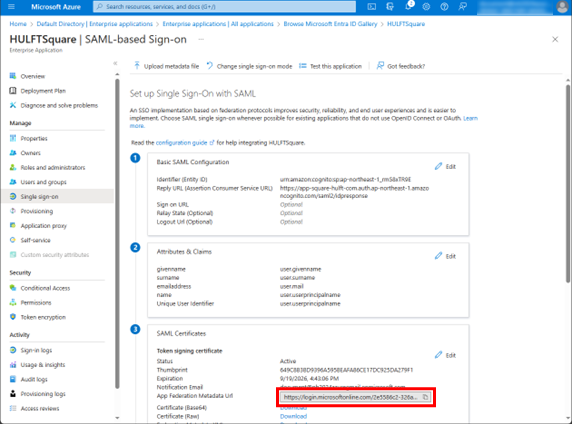
-
(4) Contact the users to convey the HULFT Square login URL
Contact the members who belong to the specific HULFT_Square_Users group and convey the HULFT Square login URL. Ask them to check whether they can log in using SSO.
On one of the following login screens, enter the email address registered in Active Directory or Microsoft Entra ID and the password for it.
-
For ADFS
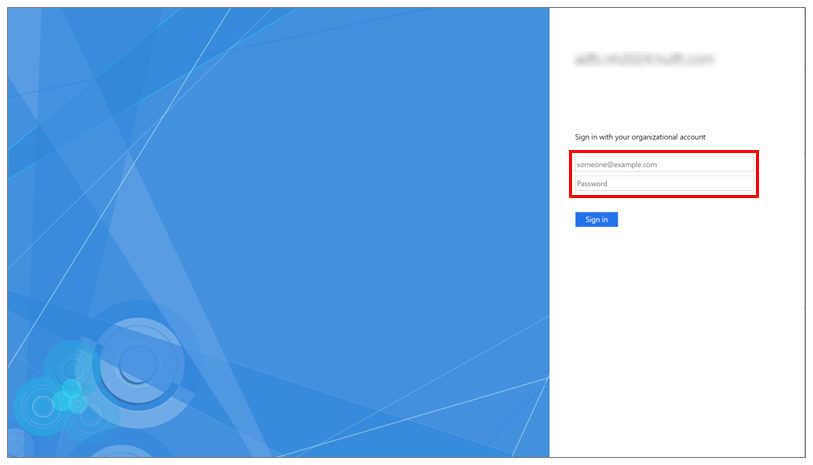
-
For Microsoft Entra ID
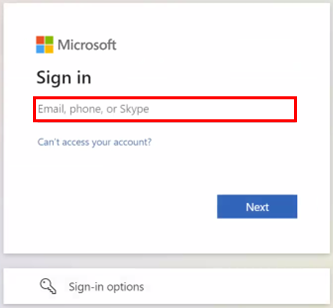
Check to make sure the users are able to log in.
Enable SSO for all groups
After confirming the usability of SSO with a specific group, enable SSO for all groups.
Inviting users when SSO is enabled
Users who have SSO enabled must be invited via SSO.
Add the users you want to invite to HULFT_Square_Users of Active Directory or Microsoft Entra ID and contact them to convey the HULFT Square login URL.
Although users who have the EditSSO permission can invite users from  > USER MANAGEMENT > Users, they should be invited via SSO as described above.
> USER MANAGEMENT > Users, they should be invited via SSO as described above.
(5) Add users to the security group of Active Directory or Microsoft Entra ID in your environment
Add all the users to the HULFT_Square_Users security group of Active Directory or Microsoft Entra ID in your environment created in step (1) .
-
Select
 > USER MANAGEMENT > Single Sign-On.
> USER MANAGEMENT > Single Sign-On. -
On the Single Sign-On page, select Edit.
-
On the edit page of Single Sign-On, specify the SSO information.
Set the following values here and select Apply.
Field name
Setting (example)
Status
On - All Groups
IdP
ADFS or Microsoft Entra ID
Email domain
Set the email domain of the organization which you belong to.
Federation metadata URL
-
For ADFS
https://<adfs-server-url>/FederationMetadata/2007-06/FederationMetadata.xml
-
For Microsoft Entra ID
Enter the value for App Federation Metadata Url under SAML Certificates.

-
(7) Contact the users to convey the HULFT Square login URL
Contact all the members added in step (5) and convey the HULFT Square login URL. Ask them to check whether they can log in using SSO.
Check to make sure the users are able to log in.