Set up ADFS to log in with SSO
HULFT Square supports single sign-on (SSO) that uses Microsoft ADFS (Active Directory Federation Service).
In order to be able to log in with SSO, first configure ADFS, and then configure SSO in HULFT Square.
This scenario describes configuration of ADFS.
Description
Points for using SSO
Because HULFT Square manages users by groups, all users must belong to a group. If a user who doesn't have a HULFT Square account logs in to HULFT Square for the first time with SSO, a user account is created when that user logs in. That user must be assigned to a group.
In this tutorial, you will create a security group to which SSO users belong on the Active Directory side and map them to the group on the HULFT Square side so the users are mapped to the specified group.
Steps and what to do
Configure ADFS with the following procedures:
Procedures
-
Create a security group called HULFT_Square_Users in the Active Directory in your environment.
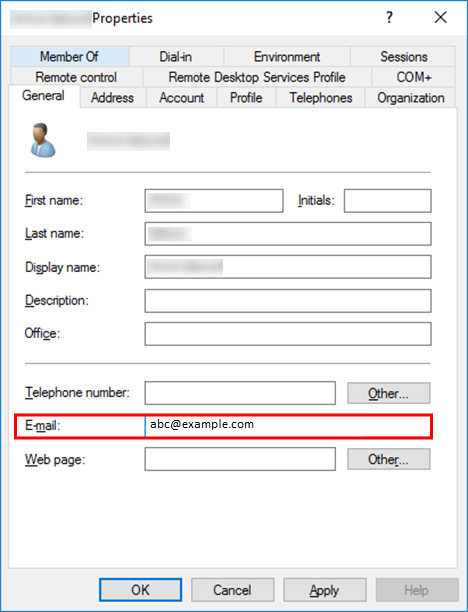
In the ADFS settings, a user's email address is used as their ID.
Because of this, make sure to set an email address in E-mail of the General tab on the following property settings screen for the Active Directory users.
-
In
 > USER MANAGEMENT > Groups of HULFT Square, create a group called HULFT_Square_Users that is assigned with the minimum of policies that all users must have.
> USER MANAGEMENT > Groups of HULFT Square, create a group called HULFT_Square_Users that is assigned with the minimum of policies that all users must have.
(2)Add a [Relying Party Trust]
To connect ADFS with HULFT Square, configure Relying Party Trusts.
-
In AD FS of the console tree, right-click Relying Party Trusts and select Add Relying Party Trust.
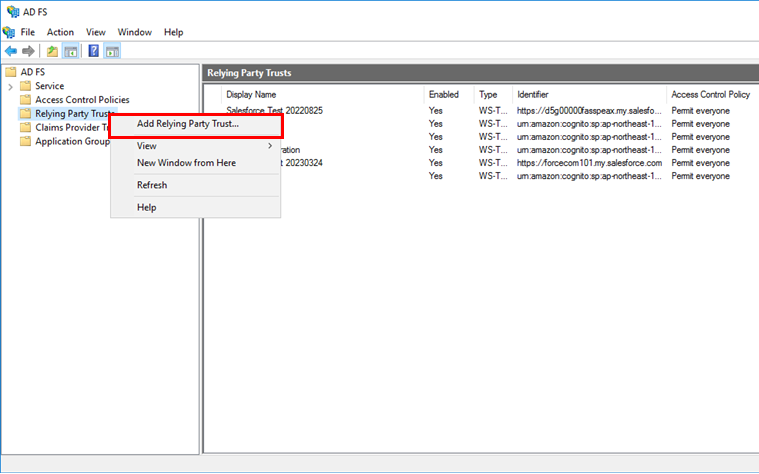
The Add Relying Party Trust Wizard screen is started.
-
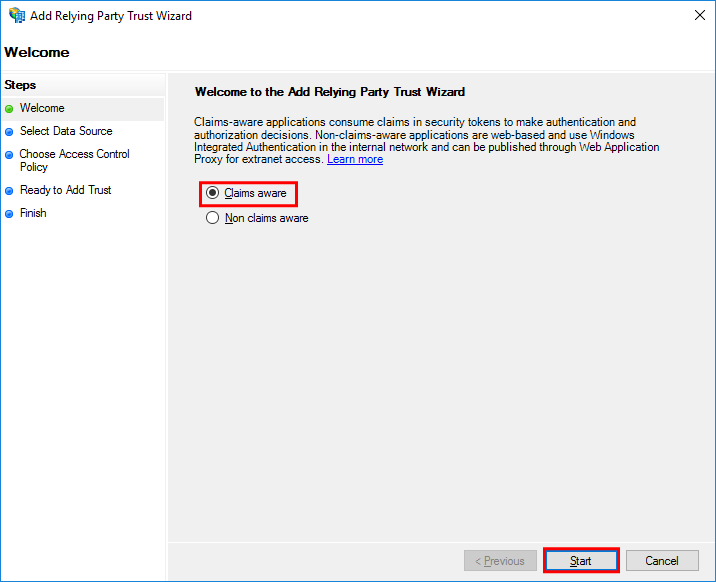
In the Welcome step of the Add Relying Party Trust Wizard screen, set Claims aware and select Start.
-
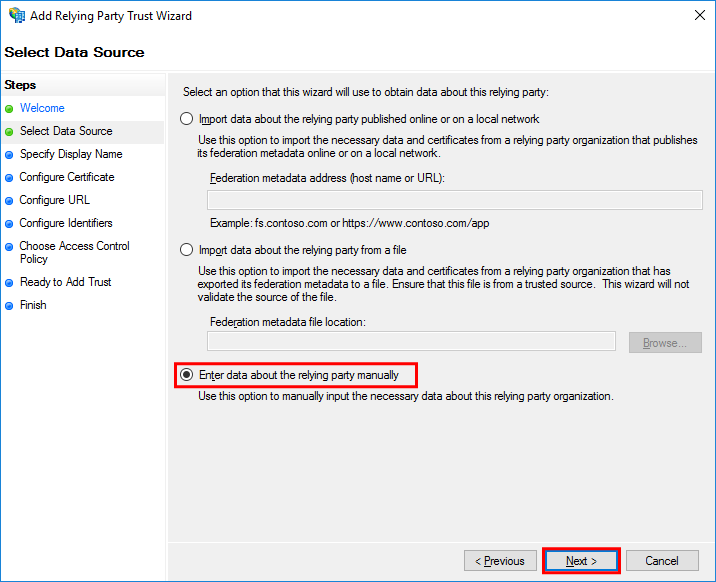
In the Select Data Source step, set Enter data about the relying party manually and then select Next.
-
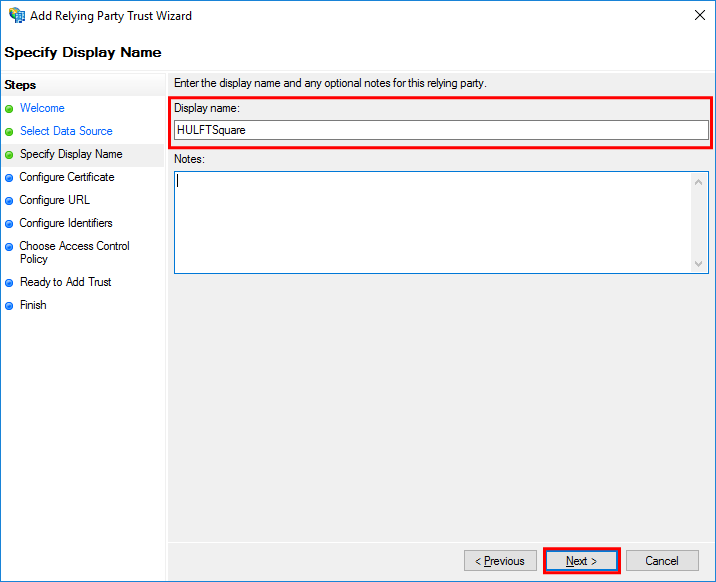
In the Specify Display Name step, specify HULFTSquare for Display name and then select Next.
-
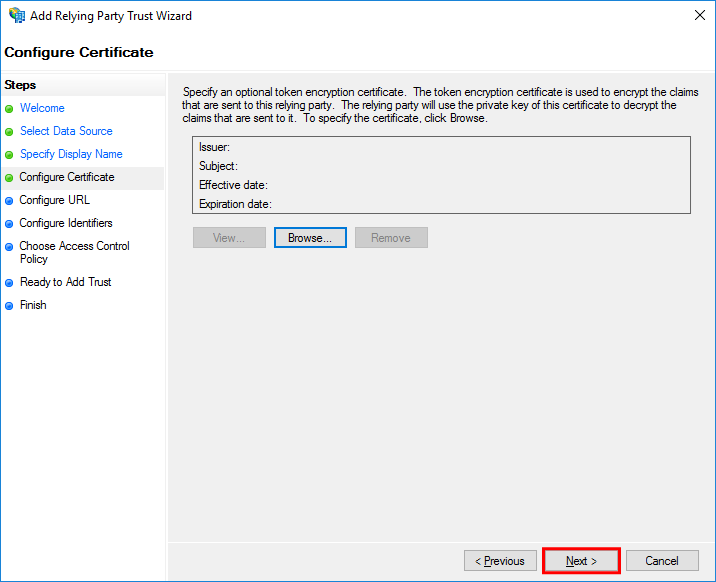
In the Configure Certificate step, select Next.
-
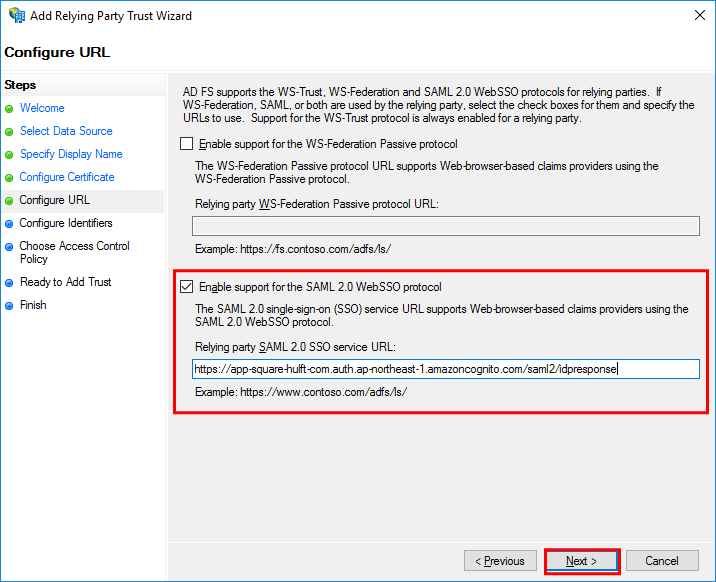
In the Configure URL step, set the fields as shown below and then select Next.
Field name
Setting (example)
Enable support for the SAML 2.0 WebSSO protocol
Select the checkbox.
Relying party SAML 2.0 SSO service URL
https://app-square-hulft-com.auth.ap-northeast-1.amazoncognito.com/saml2/idpresponse
-
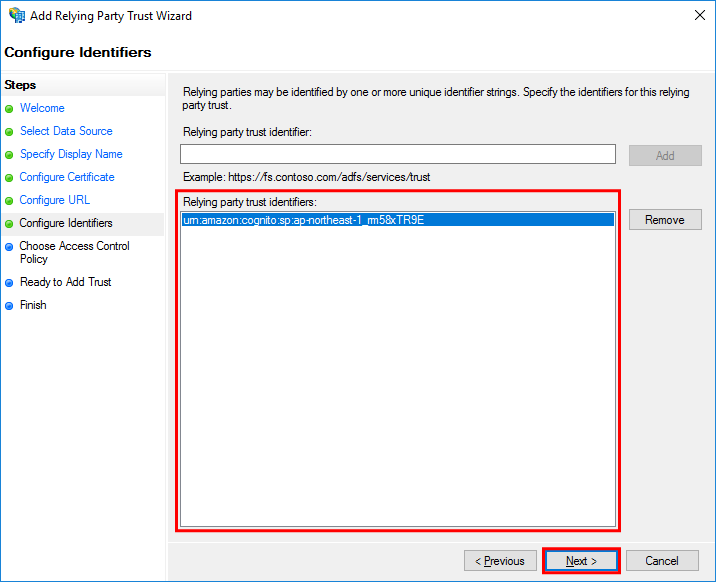
In the Configure Identifiers step, set urn:amazon:cognito:sp:ap-northeast-1_rm58xTR9E and then select Add.
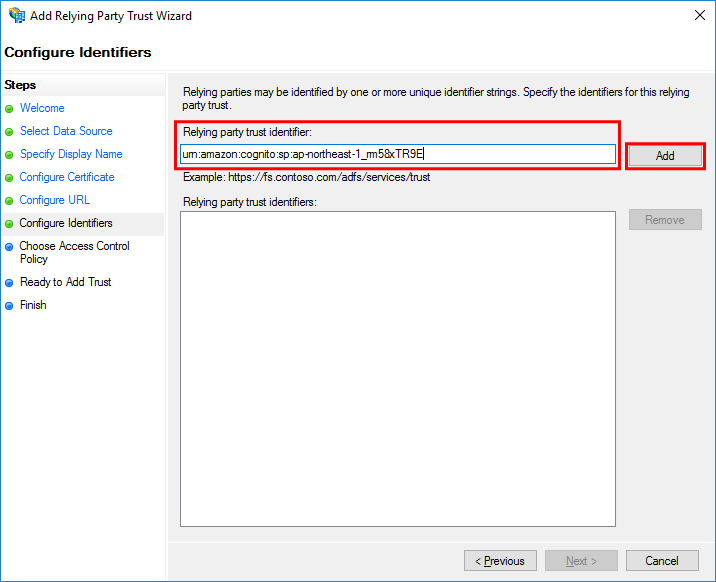
The set value is displayed in the Relying party trust identifiers list. Select Next.
-
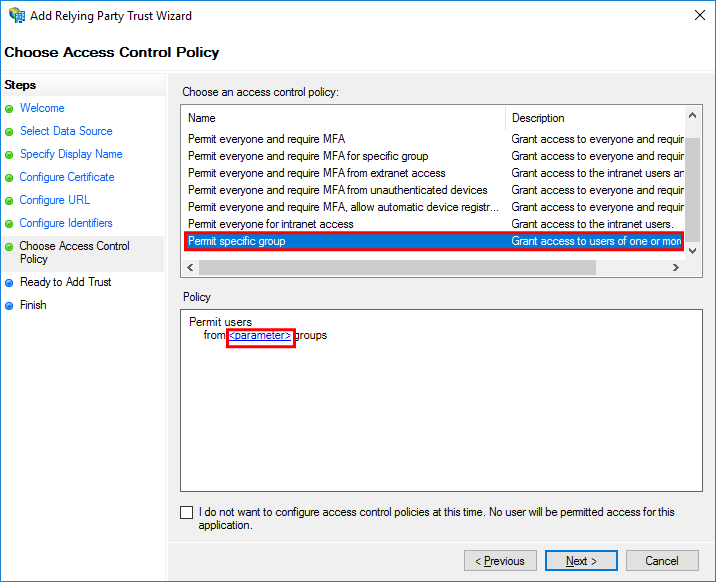
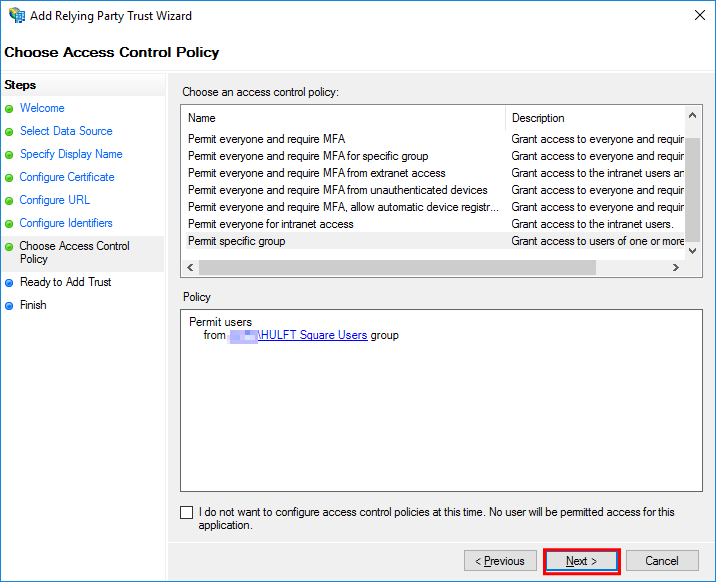
In the Choose Access Control Policy step, set Permit specific group and then select the link for <parameter>.
-
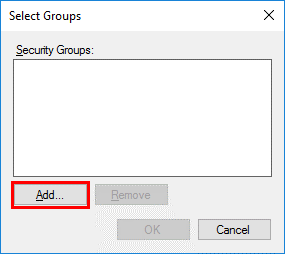
On the Select Groups screen, select Add.
-
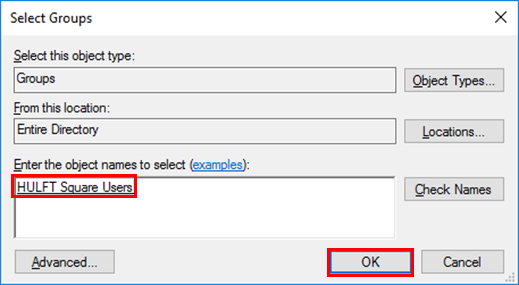
Enter HULFT_Square_Users for the selected object name and then select OK.
-
Make sure that <Domain name>\HULFT_Square_Users is displayed in Security Groups and then select OK.
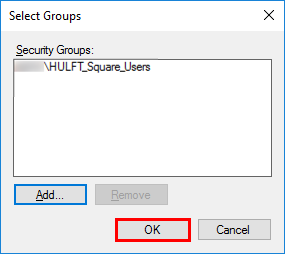
-
After you finish setting the Choose Access Control Policy step, select Next.
-
In the Ready to Add Trust step, select Next.
-
In the Finish step, select Close.
With the above procedure, a relying party trust named HULFTSquare is added.
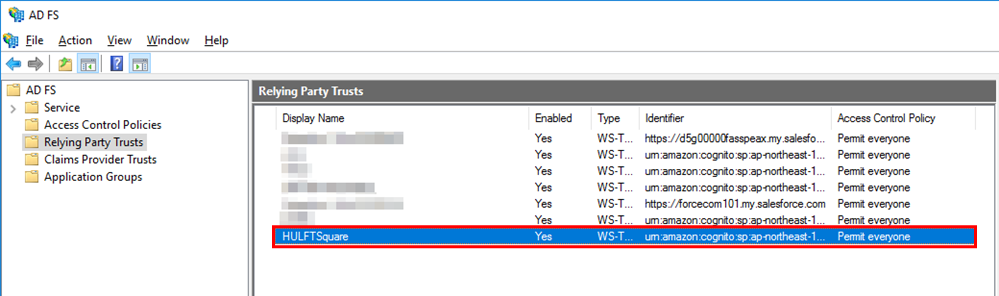
(3)Create a policy to send LDAP attributes to HULFT Square
Configure a claim issuance policy to send the LDAP attributes of email addresses, surnames, and given names from ADFS to HULFT Square.
-
From the list of Relying Party Trusts, right-click HULFTSquare and then select Edit Claim Issuance Policy.
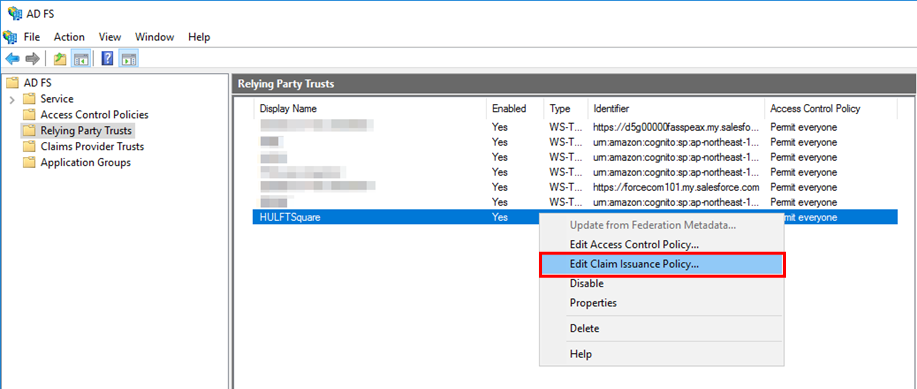
-
On the Edit Claim Issuance Policy for HULFTSquare screen, select Add Rule.
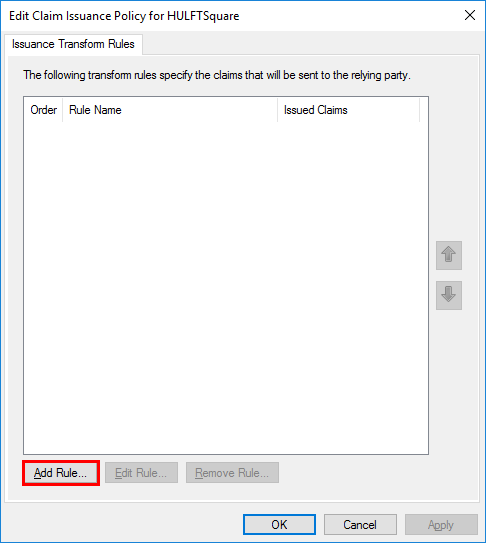
The Add Transform Claim Rule Wizard screen is displayed.
-
In the Choose Rule Type step, set Send LDAP Attributes as Claims in Claim rule template and then select Next.
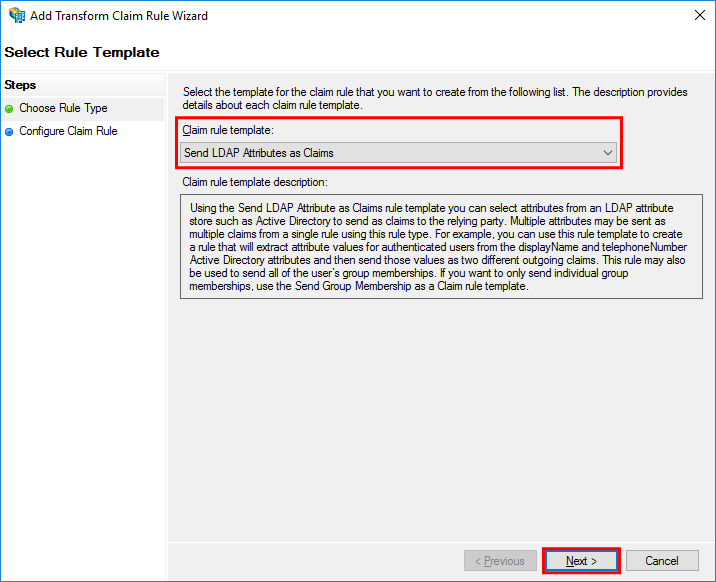
-
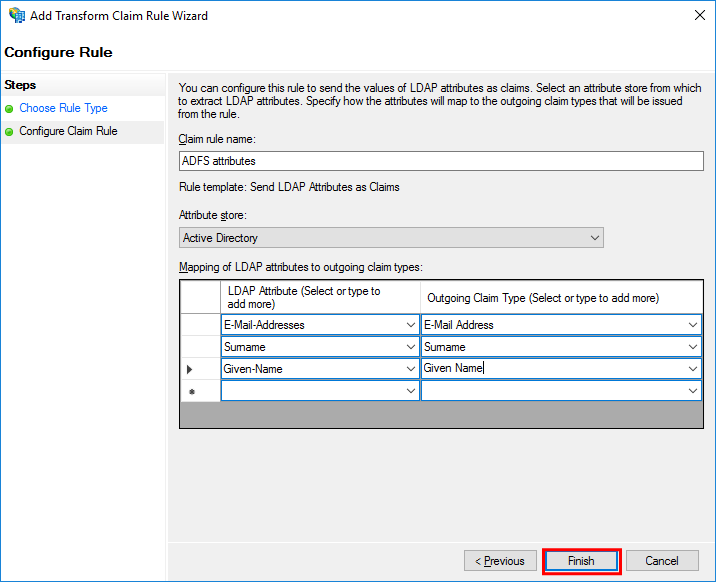
In the Configure Claim Rule step, set the fields as shown below and then select Finish.
Field name
Setting (example)
Claim rule name
ADFS attributes
Attribute store
Active Directory
Mapping of LDAP attributes to outgoing claim types
LDAP Attribute
Outgoing Claim Type
E-Mail-Addresses
E-Mail Addresses
Surname
Surname
Given-Name
Given Name
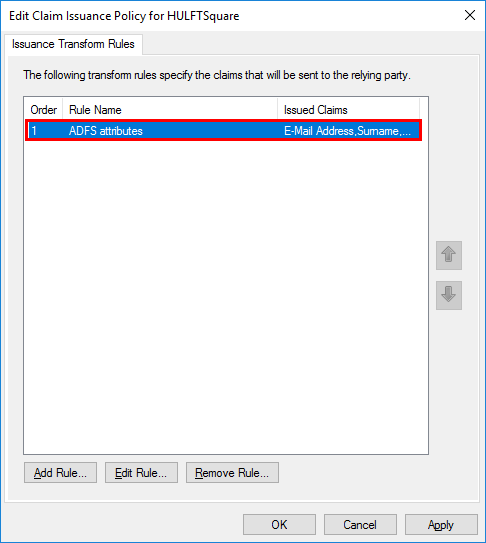
A rule named "ADFS attributes" is added to the Issuance Transform Rules tab.
(4)Map SAML email to HULFT Square email
Configure a claim issuance policy to map SAML email to HULFT Square email.
-
On the Edit Claim Issuance Policy for HULFTSquare screen, select Add Rule in the Issuance Transform Rules tab.
The Add Transform Claim Rule Wizard screen is displayed.
-
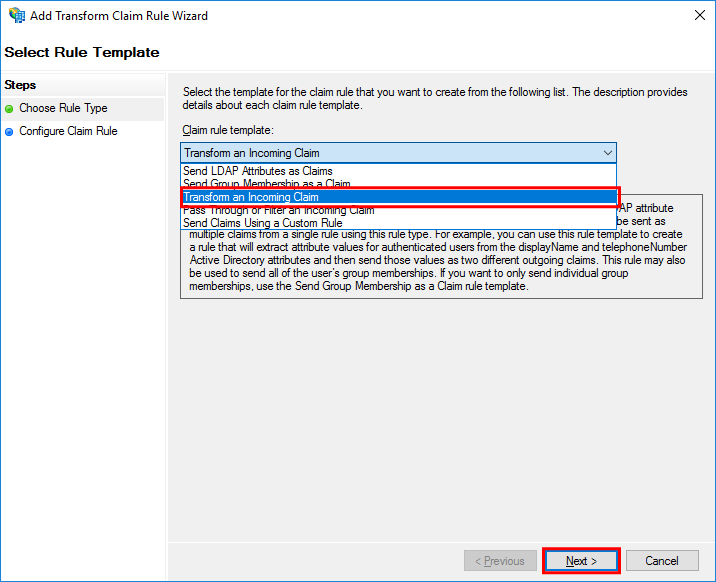
In the Choose Rule Type step, set Transform an Incoming Claim in Claim rule template and then select Next.
-
In the Configure Claim Rule step, set the fields as shown below and then select Finish.
Field name
Setting (example)
Claim rule name
Name ID
Incoming claim type
E-Mail Address
Outgoing claim type
Name ID
Outgoing name ID format
Email
Pass through all claim values
Select the checkbox.
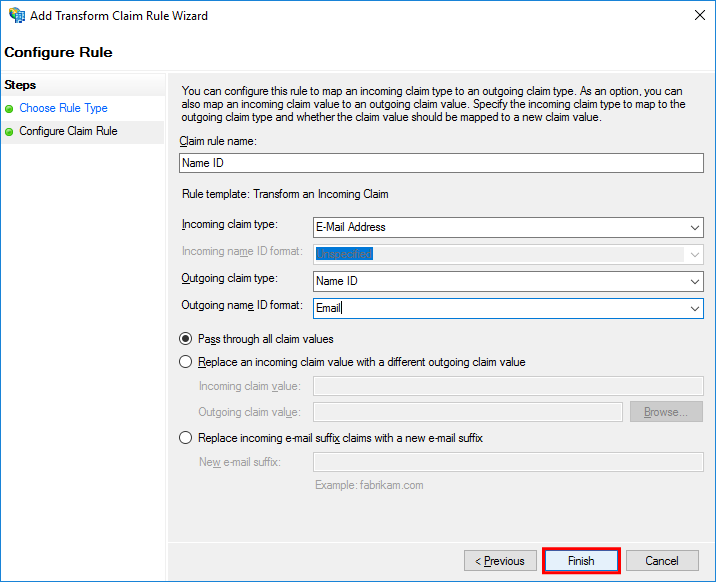
A rule named "Name ID" is added to the Issuance Transform Rules tab.
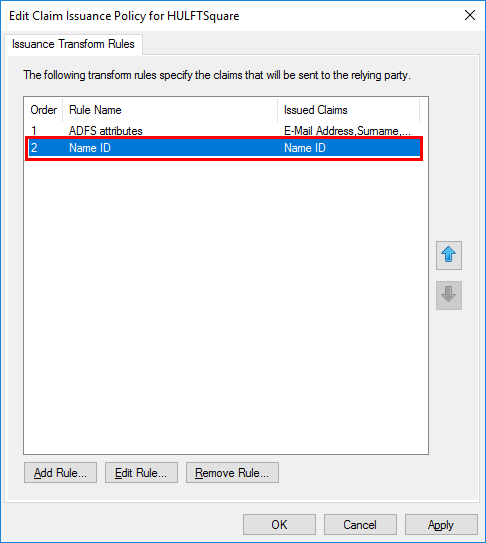
(5)Map the Active Directory group to the HULFT Square group
You can map the Active Directory group to the HULFT Square group by configuring the following settings. However, only one group can be mapped.
-
On the Edit Claim Issuance Policy for HULFTSquare screen, select Add Rule in the Issuance Transform Rules tab.
The Add Transform Claim Rule Wizard screen is displayed.
-
In the Choose Rule Type step, set Send Group Membership as a Claim in Claim rule template and then select Next.
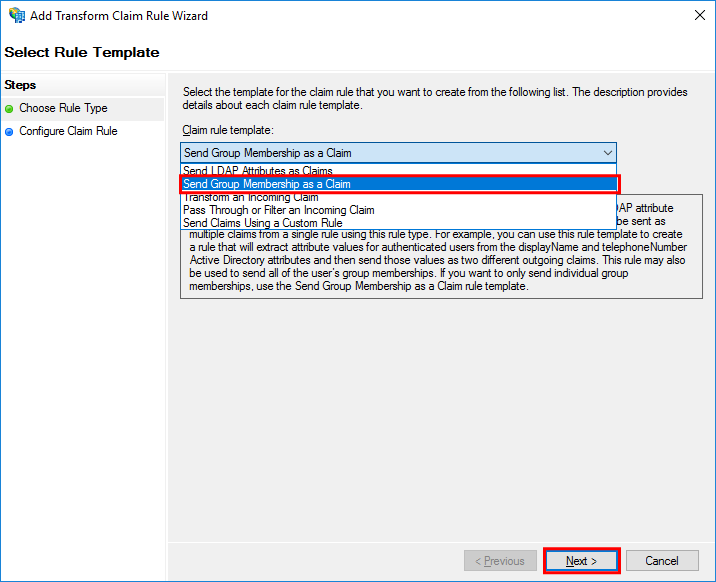
-
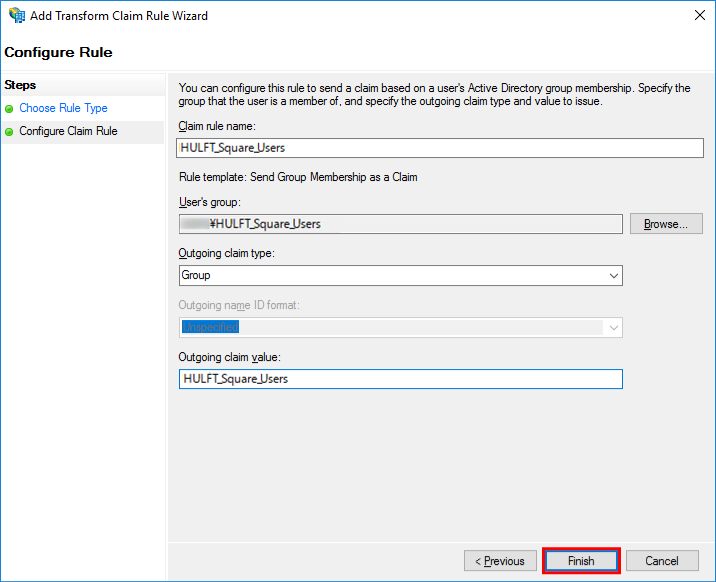
In the Configure Claim Rule step, set the fields as shown below and then select Finish.
Field name
Setting (example)
Description
Claim rule name
HULFT_Square_Users
Set a claim rule name.
User's group
<Domain name>\HULFT_Square_Users
Select a group set in Active Directory.
Outgoing claim type
Group
Select the claim type of the target.
Outgoing claim value
HULFT_Square_Users
Set the HULFT Square group name.
A rule named HULFT_Square_Users is added to the Issuance Transform Rules tab.
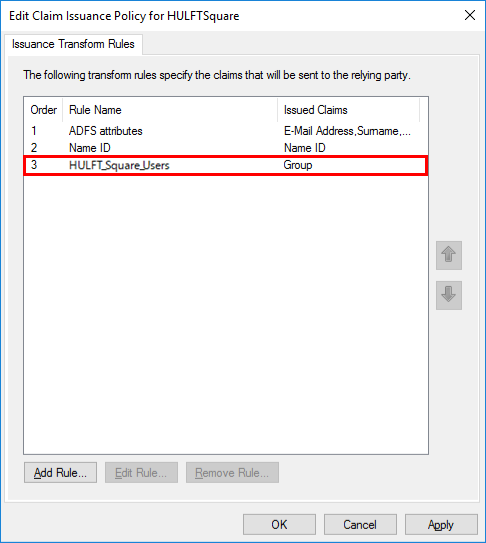
-
On the Edit Claim Issuance Policy for HULFTSquare screen, select OK.
This completes the configuration of ADFS in your environment.