File Access Log List Display command
You can display a record or records in the File Access Log file in a list format. The contents displayed are output to the standard output. You can output the contents to a file or to a printer by using the redirection symbol (greater than, >) or pipe (vertical bar, |).
The File Access Log files backed up by automatic or manual rotation become the target of this command as well.
Syntax for the File Access Log List Display command
utlopllist -fl
[-list|-csv] [-h hostname] [-usr userID|-admusr userID]
[-op operation] [-file systemfile] [-prcid processingID]
[-from Date1 [-ftime hhmmss1]] [-to Date2 [-ttime hhmmss2]]
Explanation of the parameters
- -fl
-
Specification of the File Access Log (Mandatory)
- -list|-csv
-
Output format (Optional)
- -list:
-
Main fields are output in fixed length format. For the fields to be output, refer to Table 7.1 File Access Log Fields Displayed in List.
- -csv:
-
All fields are output in CSV format. For the format of the operation logs, refer to Administration Manual.
If omitted, the fields are rearranged so that a single main field per line is output.
- -h hostname
-
Names of the starting hosts targeted for display of log records in a list format (Optional)
Specify the host name as an alphanumeric character string within 68 bytes.
When omitted, all the host names become the targets of this command.
- -usr userID
-
User ID (OS) on the starting host which is targeted for display of log records in a list format (Optional)
When omitted, all user IDs become the target of this command.
You cannot specify this parameter and -admusr at the same time.
= Remarks =User ID (OS) is subject to the conventions of the operating system on the starting host. For details on the Operation Log, refer to Administration Manual.
- -admusr userID
-
User ID of the Management Screen Security on the target starting host to be displayed in a list format (Optional)
Specify the ID as an alphanumeric character string within 32 bytes.
When omitted, all user IDs become the target of this command.
You cannot specify this parameter and -usr at the same time.
= Remarks =For details on the user IDs of the Management Screen Security of each host type, refer to the explanation of the Operation Log in Administration Manual.
- -op operation
-
Target file access type to be displayed in a list format (Optional)
When omitted, all the file access types become the targets of this command.
= Remarks =For details on the file access types that you can specify, refer to the section in Administration Manual.
- -file systemfile
-
Target system file type to be displayed in a list format (Optional)
When omitted, all the system file types become the targets of this command.
= Remarks =For details on the system file types that you can specify, refer to the section in Administration Manual.
- -prcid processingID
-
Target latest identifier to be displayed in a list format (Optional)
Specify this parameter as an alphanumeric character string in 34 bytes.
When omitted, all the latest identifiers become the targets of this command.
= Remarks =For details on the identifier, refer to the explanation of the Operation Log in Administration Manual.
- -from Date1 [-ftime hhmmss1] -to Date2 [-ttime hhmmss2]
-
Target start date (time) and end date (time) to be displayed in a list format (Optional)
Specify a numeric string within 8 bytes.
Specify the date in the format that is specified for Date Format (datefmt) in the System Environment Settings.
It is necessary to specify the date in the range of Date1<=Date2. The specified Date1 and Date2 will also be included in the list display.
Specify the time in the format of hhmmss. When Date1 and Date2 are the same date, it is necessary to specify the time in the range of hhmmss1<=hhmmss2. The specified hhmmss1 and hhmmss2 will also be included in the list display.
When you specify time by using one or both of '-ftime' and '-ttime,' the dates '-from' and '-to' are mandatory.
When both '-from' and '-to' are omitted, all the dates become the target of this command.
When you omit "-ftime", the log records at and after 00:00 on the date you specify for "-from" become the target of this command.
When you omit "-ttime", the log records up to 23:59 on the date you specify for "-to" become the target of this command.
When '-from' is omitted, all the dates up to the date specified in '-to' become targets.
When '-to' is omitted, all the dates on and after the date that is specified in '-from' become targets.
If you specify all the parameters, HULFT targets all the data within the range of Date1 and hhmmss1 to Date2 and hhmmss2.
|
Field Name |
Field Explanation |
Display Size |
|
|---|---|---|---|
|
When Output Format is |
When -list is Specified |
||
|
DATE |
Execution date and time |
23 bytes |
23 bytes |
|
PROC-ID |
Latest identifier |
34 bytes |
34 bytes |
|
OS-USERID |
User ID (OS) |
Variable |
32 bytes |
|
ADM-USERID |
User ID (Management Console) |
Variable |
32 bytes |
|
HOSTNAME |
Name of the host that started the operation |
Variable |
68 bytes |
|
OPERATION |
File access type + single-byte space + system file type |
Variable |
10 bytes + 1 byte + 25 bytes |
|
OPERATION-DETAIL |
File key information |
Variable |
40 bytes |
-
If the field string is less than the display size, the sting is displayed with left alignment.
-
When the size of a field to be displayed is larger than that of the display size, the part that exceeded the display size is cut off.
Note
-
When you specify -from, the system searches for log records with date and time from the top of the File Access Log file, and it displays the first log record and onward, of which the execution time or the execution date exceeds the specification of -from.
-
When you specify -to, the system searches for log records from the top of the File Access Log file, or from the date or time that is specified with -from, and it displays the log records up to but excluding the first one that exceeds the execution time or execution date specified by -to.
-
Records that may corrupt the format of the output log are skipped.
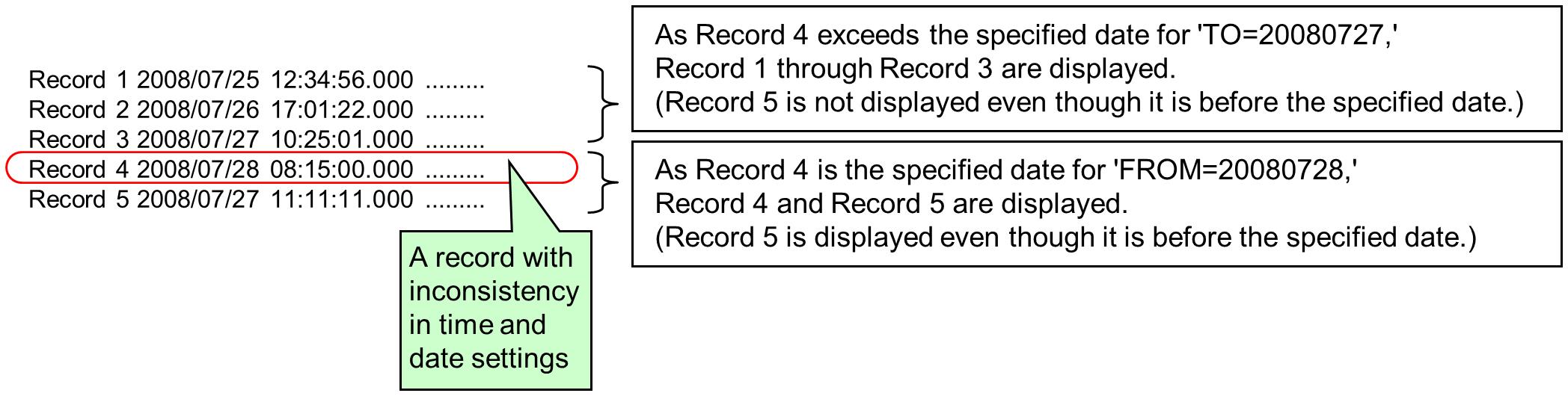
Figure 7.1 Display Range of Operation Log